Alert: TorrentLocker Mimics CryptoLocker
Another new strain of ransomware is using the “marketing” components of CryptoLocker and CryptoWall, but the coding is completely different.
This new strain is called “TorrentLocker” because of the way it is working.
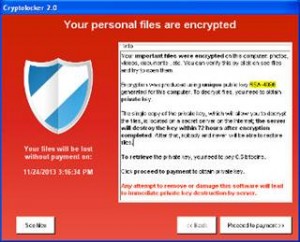
Despite its unique code, the malware tricks victims into thinking that it’s CryptoLocker by copycatting the CryptoLocker ransom message, however the design of the ransom page is made to look more like CryptoWall. The malware installs itself on the infected machine and injects a binary into a legitimate process. This injected binary contains the functionality to encrypt files using the Rijndael algorithm.
Once files are encrypted, the victim is prompted with a ransom message and a decryption deadline. The victim is required to purchase Bitcoins and send the payment to the Bitcoin address provided.
The malware and its configuration reside in the Windows Registry, in \Software\Bit Torrent App\ for continued persistence on the infected machine. The registry contains items such as the original binary, ransom message, install locations, autorun key and number of encrypted files.
Leave a Reply