ALERT: Ransomeware’s New Dangerous Tactics
CryptoWall V2.0 is now using “poisoned ads” on major sites like Yahoo, AOL and Match.com to infect unsuspecting victims’ networks.
Malicious ads are nothing new, but the second-generation ransomware using them is worrisome.
Proofpoint says “The sites themselves were not compromised; rather, the advertising networks upon which they relied for dynamic content were inadvertently serving malware”.
This means a so-called drive-by-download where the user does not have to click on anything.
Up until now, CryptoWall was spread by spam with infected email attachments and download links sent by the Cutwail botnet, which users had to click on the link.
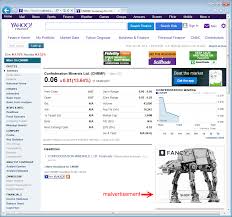
The website visitors hit by this “malvertising” are 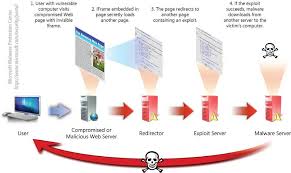 people who run unpatched versions of Adobe Flash. The poisoned ads silently ‘pull in’ malicious exploits from the FlashPack Exploit Kit, hence the “drive-by-downloads”.
people who run unpatched versions of Adobe Flash. The poisoned ads silently ‘pull in’ malicious exploits from the FlashPack Exploit Kit, hence the “drive-by-downloads”.
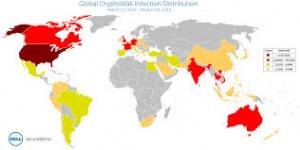
According to security researchers at Dell Secureworks, more than 830,000 victims worldwide have been infected with ransomware, a 25% increase in infections since late August when there were 625,000 victims.
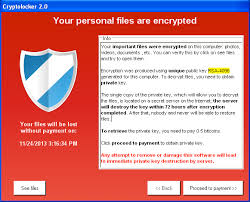
The first ransom usually has a deadline of 4-7 days, and demands around $500. Even bad guys have a conscience and understand its not always to get your hands on Bitcoins quickly. However, when this deadline passes, the ransom doubles to approximately $1000, depending on Bitcoin exchange rates.
Counting the ransom payments to CrytoWall’s Bitcoin addresses, Proofpoint estimates that the attackers make $25,000 per day. Recent data taken directly from the CryptoWall ransom payment server, shows that since August 2014, an additional 205,000 new victims have been claimed.
How To Help Prevent Infection:
1. Do not use mapped drives. Period.
Use UNC names instead to connect to servers. Apart from close to real-time (snapshot) fileserver backups, I also strongly recommend to deploy ad blockers for all the browsers in your organization, if you have not done so already. Or make sure you use endpoint security that has ad-blocking built-in.
2. Continue to focus on all endpoints being fully patched, Windows and all third-party apps.
Also, configure endpoint browsers to only execute plug-in content when clicked, rather than automatically. Uninstall apps that are not absolutely needed, make you attack surface as small as possible.
3. Click-to-Play & Whitelisting.
Some browsers like Google Chrome and Mozilla Firefox allow you to enable click-to-play for plug-in based content, which can stop the automatic execution on exploits that target browser plug-ins. Deploying a whitelisting product on all machines is also something you could look at – whitelisting will stop ransomware cold.
4. Lifecycle Malware Detection
Technologies for lifecycle malware detection carry different names, including targeted threat protection (TTP), targeted attack protection (TAP), and “click-time link scanning”. Whatever you call it, you want it in place.
5. Company-Wde Internet Acceptable Use Policy
Having an Acceptable Use Policy (AUP) in place that forbids employees to use their machines for private browsing and have an edge device that blocks selected groups of websites (like all social media) is also something you should have in place.
6. Prepare Yourself.
You could also open an account with coinbase.com get approved (it takes a few days), create a wallet, and buy a few Bitcoin “just in case” you get hit and your backup fails.
7. Prepare Your Employees.
And obviously stepping all employees through effective security awareness training is a must these days.
Ask About Our Affordable ‘Core Security’ Plan

Leave a Reply