ALERT:
New Ransomware Infection “LowLevel04”, Coming Soon to a Computer Near You!
The new ransomware called “LowLevel04”, infects your computer, and encrypts your files making them useless to you…unless you pay their ransom demand for a decryption code.
(Hint: Backup your important files. Check out our Managed Backups – they could save your company!)
What’s different about this new version? For one, the ransom demanded is double the ‘normal’ $500, and demands 4 Bitcoin. Many victims have also reported that the machines affected were servers, which could cause pandemonium within (or bankrupt) a company.
Larry Abrams (from techie blog Bleeping Computer”) was the first to report on the new strain. He stated:
“It appears that once the attacker gains access to a target computer, they download and install a package that generates the encryption keys, encrypts the data files, and then uploads various files back up to the hacker’s temp folder via a terminal services client drive mapping file”.
LowLevel04 scans all mapped drives, including removable and network drives, for data files to encrypt. When it encounters a file that contains certain file extensions it will encrypt them. When it’s finished wreaking havoc, the malware cleans up after itself and deletes a number of files used in the encryption process, as well as removing application, security, and system logs.
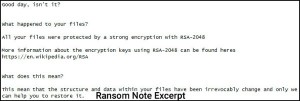
In each encrypted folder, a ransom note is found. The note has instructions for the victim to follow, if they want to decrypt their files.
NOTE:
Abrams does mention that LowLevel04 does not delete Shadow Volume Copies (yet), so you could use that to get original, unencrypted versions of files back.
How To Avoid Becoming A Victim
Ransomware CyberCriminals have used RDP (Remote Desktop Protocol) exploits to gain access in the past, because so many businesses use remote desktop on a daily basis. So here’s how to avoid becoming yet another victim of ransomware:
- If You Don’t Need It, Disable It: It’s a good rule of thumb for everything. Leaving anything enabled, when you don’t use it, is just leaving another potential back door open for CyberCriminals to gain access to your computer/network. If you don’t use RDP, disable it. It’s a huge CyberSecurity hazard.
- Keep Patches Up-To-Date: Again, good rule-of-thumb for any electronics that are connected to the Internet (even just for short periods of time). Keeping Windows patched will help ward off potential RDP exploits.
- Use What You’re Comfortable With: If you’re not comfortable with something, you’re not going to use it. This goes for RDP as well. If you’re uncomfortable with the out-of-the-box functionality provided by Windows remote desktop software, change to another software you are comfortable with. Talk to your I.T. provider about options.
- Use Additional Safety Measures: Sure, your network security may be good. But remote desktop is such a huge CyberSecurity hazard that you should have additional security measures in place for each user/computer. Especially with all the recent hacking, a 2-factor authentication for all remote logins is a absolute MUST.
- Security Awareness Training: Many of the ransomware attacks still arrive via email. Anyone that has access to anything that contains, or has access to information and the Internet is a CyberSecurity risk and should be put through Security Awareness Training. This includes everything from computers to mobile devices and receptionist to accountant to CEO.
- Backup, Backup, Backup: The surest solution for that applies to everyone, from the home user to the biggest corporation – BACKUPS. No defense plan is foolproof – so backup anything you don’t want to chance losing. Did I mention backups?
Not sure if your company is safe? Ask us for a FREE Network Security Assessment!
Check out our “Email Red Flags” for what to watch for, in suspicious emails.
Ask us about our “Core Security Solutions” package!

Leave a Reply