ALERT:
A $46 Million CyberHeist…and Why You Should Care
Late last week, Networking firm Ubiquity Networks Inc. disclosed that CyberCriminals recently stole $46.7 Million using an increasingly common scam using spear-phishing.
Targeting businesses using spear-phishing isn’t a new tactic of CyberCriminals (see past ALERTs: Resume Ransomware, Banking Email Scam, Email Attachment “Fax”, etc.), but it has become increasingly common.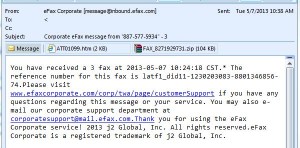
In this specific CyberHeist, CyberCriminals used fake communications from “executives” at the victimized firm in order to initiate unauthorized international wire transfers. Ubiquity, a San Jose, USA networking technology maker for service providers and enterprises, disclosed the attack in a quarterly financial report, which they filed this week with the U.S. Securities and Exchange Commision (SEC). Ubiquity states is discovered the fraudulent CyberHeist on June 5/15, and reported that the incident involved employee impersonation and fraudulent requests from an outside entity targeting the company’s finance department. Ubiquity stated:
“This fraud resulted in transfers of funds aggregating $46.7 million held by a Company subsidiary incorporated in Hong Kong to other overseas accounts held by third parties…As soon as the Company became aware of this fraudulent activity it initiated contact with its Hong Kong subsidiary’s bank and promptly initiated legal proceedings in various foreign jurisdictions. As a result of these efforts, the Company has recovered $8.1 million of the amounts transferred.”
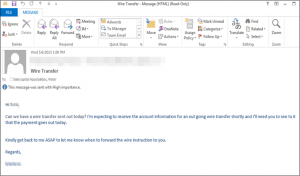 Previously known as “CEO Fraud“, and “Business Email Compromise“, the CyberHeist that hit Ubiquity is a sophisticated, and (unfortunately) increasingly common one, targeting businesses working with foreign suppliers and/or businesses and that regularly use wire transfer payments. In January 2015, the FBI warned the public about CyberHeists that resulted in CyberCriminals stealing almost $215 million from businesses in the previous 1 1/2 years. In those CyberHeists, the CyberCriminals spoofed or hijacked email accounts of company business executives or employees.
Previously known as “CEO Fraud“, and “Business Email Compromise“, the CyberHeist that hit Ubiquity is a sophisticated, and (unfortunately) increasingly common one, targeting businesses working with foreign suppliers and/or businesses and that regularly use wire transfer payments. In January 2015, the FBI warned the public about CyberHeists that resulted in CyberCriminals stealing almost $215 million from businesses in the previous 1 1/2 years. In those CyberHeists, the CyberCriminals spoofed or hijacked email accounts of company business executives or employees.
Although Ubiquity did not disclose how they were victimized, usually CyberHeists of this kind are performed using spear-phishing company employees to first gain information about the company’s upper echelon, as well as information about which employees have access to and/or regularly perform financial transactions/wire transfers with suppliers/other businesses. They then either send fake emails spoofing those upper echelon or the employees (previously mentioned), in order to gain access to, or spoof wire transfers. In any case, the CyberCriminals are in search of money.
Why You Should Care
I know, you’re wondering what any of this has to do with you, because your business doesn’t have $46 million to lose…But that’s just it. $46 million obviously didn’t bankrupt Ubiquity, but a much smaller amount might bankrupt your business.
In any of these cases, ANY of these victimized companies could have been prevented by effective Employee Security Awareness training.
Think of all the Internet/I.T. security a big company like Ubiquity likely has…and the CyberCriminals still got in. Now think of the Internet/I.T. security your company has…scared yet? No, the bad guys that went after Uqibuity likely won’t come after your company. BUT there are CyberCriminals that are lower on the CyberHeist skill level scale that ARE targetting companies…JUST LIKE YOURS. And there are MORE of these CyberCriminals out there.
Not sure if you’re company is safe? Ask us for a FREE Network Security Assessment!
Check out our “Email Red Flags” to see a general indication of, and what to watch for, in suspicious emails.
Ask us about our “Core Security Solutions” package!

Leave a Reply