 ALERT: FBI Public Alert
ALERT: FBI Public Alert
The FBI released a warning recently against a new CyberCriminal I.T. crime wave that is so prevalent and so devastating to companies, that the FBI have named it:
“CEO Fraud”
This scam is also known as “Business Email Compromise“, which we sent out an ALERT for in January. 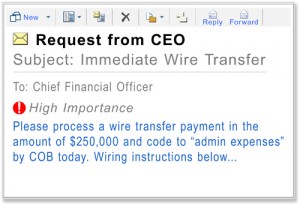
“CEO Fraud”: CyberCriminals impersonate a company’s CEO, using the company’s own spoofed domain name. The fake CEO contacts company employees in charge of money transfers, and orders them to transfer large amounts of money out of the country.
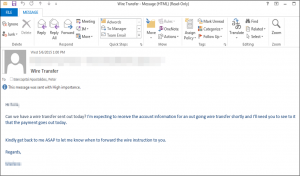 CyberCriminals take employee email addresses and other information from the target company’s website to help make the emails more convincing. In the case where executives or employees have their inboxes compromised by the thieves, the crooks will scour the victim’s email correspondence for certain words that might reveal whether the companies routinely deals with wire transfers (searching for messages with key words like “invoice”, “deposit” or “president” or “CEO”).
CyberCriminals take employee email addresses and other information from the target company’s website to help make the emails more convincing. In the case where executives or employees have their inboxes compromised by the thieves, the crooks will scour the victim’s email correspondence for certain words that might reveal whether the companies routinely deals with wire transfers (searching for messages with key words like “invoice”, “deposit” or “president” or “CEO”).
CyberCriminals monitor the email account of a company’s CEO for months, waiting for the right time to kick this fraudulent event off. The “right time” is usually a time where the CEO is out of town, or can’t be easily reached.
The CyberCriminals spoof the name of the company’s own domain (eg. “tbyd.co” instead of “tbyd.ca”) to make the emails more convincing, which can be done easily if your email server is not configured properly.
(One reason to get a professional I.T. organization to manage and maintain your I.T. network!)
The CyberCriminals, once they have spoofed the company’s domain, and have confirmed (by monitoring the CEO’s email account) that the CEO cannot easily be reached for confirmation, send URGENT emails that look legit. The emails look like they are coming directly from the CEO, and are ordering the employee to send wire transfers.
This email fraud is targeting small and medium-sized companies, and the current loss is tallied at $1.2 Billion.
“The scam has been reported in all 50 states and in 79 countries,” the FBI’s alert notes.
“Fraudulent transfers have been reported going to 72 countries; however, the majority of the transfers are going to Asian banks located within China and Hong Kong.”
How To Prevent Becoming a Victim
The FBI suggests the following tips for businesses to avoid being victimized by this scam (a more complete list is available at: www.ic3.gov).
- Verify changes in vendor payment location and confirm requests for transfer of funds.
- Be wary of free, web-based email accounts, which are more susceptible to being hacked.
- Be careful when posting financial and personnel information to social media and company websites.
- Regarding wire transfer payments – Be suspicious of requests for secrecy or pressure to take action quickly.
- Consider financial security procedures that include a two-step verification process for wire transfer payments.
- Create intrusion detection system rules that flag emails with extensions that are similar to company email, but not exactly the same. For example “.co” instead of “.com”.
- If possible, register all Internet domains that are slightly different than the actual company domain.
- Know the habits of your customers, including the reason, detail, and amount of payments. Beware of any significant changes.
Not sure if your company is safe? Ask us for a FREE Network Security Assessment!
Check out our “Email Red Flags” for what to watch for, in suspicious emails.

Leave a Reply