Alert: More Celeb Misfortunes
There is a new current event, which is unfortunately going to be the new click bait for CyberCriminals.
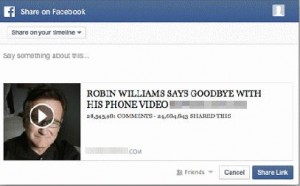
Apple’s iCloud has been hacked. As a result, the account of Jennifer Lawrence, as well as many other celebrities have been ‘outed’. Apparently, Jennifer Lawrence had taken nude photos of herself and the photos are now out and about on the internet.
Apple has patched a bug that would allow brute force attacks on iCloud, which may have been how the hack was done.
The cyber mafia are already working on campaigns to exploit Jennifer Lawrence’s misfortune, and there will be some interesting phishing attacks over the next few months regarding this.
CyberCriminals are going to use this ‘scandal’ to use people’s curiosity against them by tricking them to click on links and open attachments, which will infect their computer with malware.
Remember: “Curiosity killed the cat”…
Ask About Our ‘Core Security’ Package!



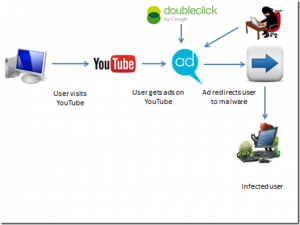
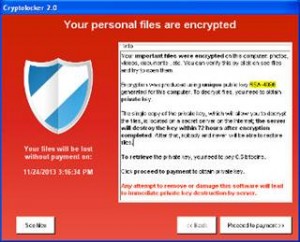
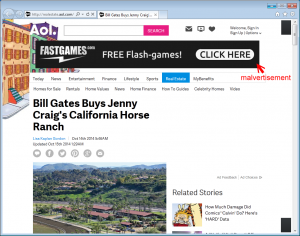 first video causes a redirect, an exploit kit located on a compromised website kicks in, finds a known unpatched vulnerability, and once found, executes ransomware code which locks all files and extorts $500. These exploit kits check for hundreds of known holes in mere seconds, so the “ad-network” threat just escalated to a much higher level.
first video causes a redirect, an exploit kit located on a compromised website kicks in, finds a known unpatched vulnerability, and once found, executes ransomware code which locks all files and extorts $500. These exploit kits check for hundreds of known holes in mere seconds, so the “ad-network” threat just escalated to a much higher level.