Double-Ransomware Attack
A new, and very scary ransomware strain has surfaced, called Goldeneye. It encrypts the workstation TWICE: First it encrypts the files, then it encrypts the Master File Table.
The attack is received as spam phishing email (HINT: Need a Spam Filter!), and presents itself as a job application form to be filled out. Attached is an infected PDF with the “application” which claims will get the process started. In the PDF is a polite reference to the also attached Excel file, which it states “contains more details”.
When the victim opens up the Excel file, they get a suggestion on how to display the “aptitude test”.
Sophos, the company that first reported Goldeneye, states,
“The crooks don’t openly ask you to do anything obviously risky, such as “Enable macros” or “Turn off the default security configuration”, but they do encourage the victim to make a change to their Office settings, something that Excel will invite you to do because the file contains what are known as Visual Basic for Applications (VBA) macros.
If you permit macros to run in this Excel file, you will quickly regret it. The VBA downloads a copy of the Goldeneye ransomware, and immediately launches it.”
The VBA programming language used in Office macros is powerful enough to allow CyberCriminals to control Word or Excel progammatically, but also to perform more general functions…such as downloading files from the web, saving them to disk, and running them.
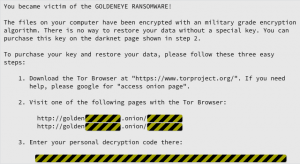
Once the Excel file is activated, all the malicious activity happens in the background. However, when the encryption is completed, there’s a whole bunch of files left behind called: “YOUR_FILES_ARE_ENCRYPTED.TXT”, which announces the infection:
Most file-encrypting ransomware strains stop here. But Goldeneye’s developer has experience, and does a double-whammy attack similar to their Petya/Misha strain and encrypts the Master File Table (MFT) of that machine as well.
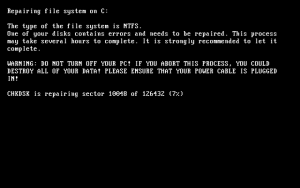
Goldeneye works a bit different than previous strains in that first it encrypts the files, then performs a “UAC bypass” and the low-level MFT attack, then reboots and pretends it’s doing a CheckDisk.
Once the “check” is finished, another reboot sounds the alarm with some rather dramatic ASCII art:
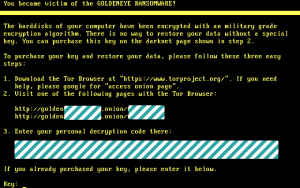
Pressing the “Any Key” (anyone else hear Homer Simpson in their head right now?) gives you this:
**In case you’re wondering why Sophos redacted the so-called personal decryption codes in the images above, the encryption is different for your files and for your MFT: the malware uses different algorithms and different keys each time.**
Long story short, if you pay to unlock your scrambled MFT so you can reboot into Windows, then (assuming the CyberCriminals actually send you the decryption key) you’ll get back into Windows only to face the “YOUR_FILES_ARE_ENCRYPTED.TXT” pay page as well.
If you don’t have reliable backups, you get to pay 1.4 Bitcoins all over again.
Yes, that’s 2.8 Bitcoins total, which starts to get very expensive!


Leave a Reply