Adult Friend Finder (AFF) Hack Affects Businesses
Last week, news broke that the Adult Friend Finder (AFF) website was hacked. The site bills itself as a “thriving sex community”, and as a result users often share sensitive sexual information when they sign up. This is one of the top adult websites for people that want casual encounters, possibly cheating on their spouse. The site is one of the most heavily trafficked websites and has 63 million registered users worldwide. 
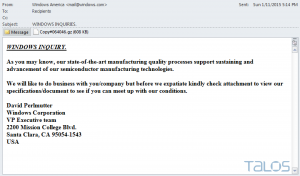
Now millions of these records are now in the open, exposing highly sensitive personal information. Internet CyberCriminals are going to exploit this in many ways, sending spam, phishing, and possibly blackmail messages, using social engineering tactics to make people click on links or open infected attachments. Be on the lookout for threatening messages like this that slip through and delete them immediately.
This is not an easy one. It only takes one second for a worried person to click on a link in an email and expose the whole network to attackers. I suggest you send this link to this post, in order to warn people not to take the bait.
The Background Story:
The story goes that the AFF site owed $240,000 to someone, likely an affiliate that was feeding them webtraffic, and supposedly the AFF did not pay their bill. The affiliate had a hacker buddy who calls himself ROR[RG], and this guy decided to teach AFF a lesson.
ROR[RG] hacked them, exfiltrated at least 4 million records and then sent them a ransom demand of $100,000 to return the data. Apparently AFF did not pay again, and in retaliation, ROR[RG] posted the stolen data on a Darknet Tor site loaded with a ton of highly sensitive, personal information. The stolen data includes their age, procreation preferences, state, zip code, username, IP address, email address, usernames, dates of birth, marital status, sexual preferences, and whether they are looking for a “cheating one night stand” or more “unorthodox” procreation activities. With a little digging, these people are easy to find.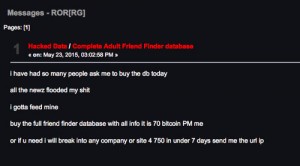
FriendFinder Network, a California-based company, hired a public relations company specializing in cybersecurity, and released this statement:
“FriendFinder Networks Inc…understands and fully appreciates the seriousness of the issue. We have already begun working closely with law enforcement and have launched a comprehensive investigation with the help of leading third-party forensics expert. We cannot speculate further about this issue, but rest assured, we pledge to take the appropriate steps needed to protect our customers if they are affected.”
The company could not be reached for further comment. UK TV Channel 4 reported it first, and stated exposed email addresses are receiving spam. Here is their 4-minute segment: http://www.channel4.com/news/adult-friendfinder-dating-hack-internet-dark-web.
The Problem:
The problem is, that any of these 40 million registered users are now a target for a multitude of social engineering attacks. People that have extramarital affairs can be made to click on links in emails that threaten to out them. Or phishing emails that claim people can go to a website to find out if their private data has been released. This is a nightmare that will be exploited by all facets of CyberCriminals: spammers, phishers, and blackmailers. All of which are rubbing their hands together in gleeful greediness. Undoubtedly jilted spouses, divorce attorneys and private investigators are already pouring over the data to see if it’s of any use to them.
How it Affects Your Business
&
What You Need To Do:
Take immediate preventive action. It only takes one second for a worried end-user (any employee with computer access) to click on a link in an email, and expose the entire network to attackers.
I suggest you send the link to this post to friends, family, coworkers, and employees, in order to warn people not to take the bait. Explain that you are sending a mass email to everyone, without judgement, in order to protect them from further attacks. Warn them that clicking on the link in an email has far worse implications.
You can’t stop CyberCriminals from targeting your company or employees.
But you can be prepared for their arrival, and have full shield up.
Got CyberBugs?
Call 1-204-800-3166
For Cyber-Extermination!







 Plug-and-Play: Just connect to wall outlet and internet router
Plug-and-Play: Just connect to wall outlet and internet router




 Review:
Review:
 You can set your phone to receive ‘notifications’ whenever a sensor is triggered, even when the system isn’t armed. However, unless you really need to know when a door or window is opened (and closed again), I wouldn’t use this. I ended up getting over 400 notifications in the 1st day & it got a little annoying. What is nice, that if you want to keep track of when they get home (and either they have one of the remote tags, or the app on their phone), you can still see when they get home, and you can always check if a door or window is open or closed.
You can set your phone to receive ‘notifications’ whenever a sensor is triggered, even when the system isn’t armed. However, unless you really need to know when a door or window is opened (and closed again), I wouldn’t use this. I ended up getting over 400 notifications in the 1st day & it got a little annoying. What is nice, that if you want to keep track of when they get home (and either they have one of the remote tags, or the app on their phone), you can still see when they get home, and you can always check if a door or window is open or closed. 



 Premium Package: Recommended for a medium sized house.
Premium Package: Recommended for a medium sized house. and save them to the cloud to access later.
and save them to the cloud to access later.


 ALERT:
ALERT: