I am an older adult that is stuck in my ways. My computer is on XP. My neighbour told me that I have to upgrade to a newer “OS” (?). I don’t want to have to learn a new program. All I use my computer for is emails, internet banking, and playing a couple of games. Do I really need to upgrade?
Sincerely,
Can’t Teach An Old Dog New Tricks
Dear Old Dog,
I completely understand not wanting to learn a new program. That is not exclusive to older adults – most people don’t want to learn a new program, and resist until they absolutely have to. Unfortunately this is one of those times. In order for me to tell you why you need to upgrade, I need to give you some background information:
‘OS’ refers to ‘Operating System‘. This is software that manages computer hardware and software resources, and provides common services for computer programs. Other software programs usually require an OS to be able to run on your computer. Most times, an OSs ‘bugs’ or security issues are not discovered until the OS is in use by the general population.
OS manufacturers release ‘patches‘ to fix these ‘bugs’, which are released to users in the form of ‘updates‘. A patch is a piece of software designed to update a computer program or its supporting data, to fix or improve it. This includes fixing security vulnerabilities and other bugs, improving the usability or performance. Generally, updates are released on Tuesdays.
OS system updates often address security vulnerabilities that have been discovered or not previously disclosed. If OS system updates are not installed in a timely manner it can lead to unauthorized access to your computer, theft of personal, confidential, or Protected Health Information, or the destruction of information, files, or pictures that are on your computer. Your computer should be set up to receive automatic updates, and should notify you when new updates are available and ready for downloading and/or installing. When the installation is completed, the computer may require you to ‘restart’ your computer to activate the newly installed updates.
OS support (patches and updates released by the manufacturer) is available for 5 years after their GA (general availability) dates, as a general rule. After those 5 years, the manufacturer no longer releases patches/updates for that OS, which leaves it vulnerable for hackers to access your computer.
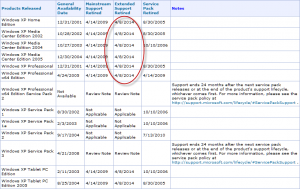
To find a Microsoft Product’s end-of-support date, use the Microsoft Product Lifecycle Search page to get the official answer. Enter the name of the OS, and click ‘Search’. You will get back a table that shows the general availability date, the retirement dates for mainstream and extended support, and retirement dates for service packs (which don’t follow the general rules of support).
Here’s the search result for Windows XP:
The date that matters most on this chart, is the one circled in red – April 8, 2014. This is when support ended for Windows XP.
What this means to you: Your computer, and everything it contains including your emails, internet banking information, and any pictures or other personal information you may have, is vulnerable to being accessed by computer hackers. So, long-story-short: yes, you need to upgrade…immediately. If you think your computer is too “small potatoes” for hackers, think again. It’s actually very easy for a hacker to hack into a computer that is vulnerable, like yours. Any low-level, low-skill hacker (ie the teenager down the street) can hack into a computer such as yours…and will.
I suggest you upgrade your OS immediately. If you can’t afford to upgrade your computer, keep all personal information off of it – emails, banking information, etc etc, and keep your computer strictly for playing solitaire. I know, this makes your computer a very large paperweight. Another option: sometimes, you can get a refurbished computer for much cheaper than a brand-new one. This would most likely not be available from any of the big-box stores – they want to sell you the newest computer out there. Judging from your general use, you don’t need a high-powered super fast computer (that would be more suited to playing the new computer games with lots of graphics). Just a reliable, and up-to-date one.
Need a new computer, or upgrade your old one?
Call Technology by Design at 1-204-800-3166 www.itthatworks.ca.
We don’t sell you what we want – We sell you what you NEED.
We’ll tell you what you need, based on use and budget. Then, we’ll tell you if your old computer is worth upgrading, or if you should invest in a newer computer.