 Like-Farming Scams:
Like-Farming Scams:
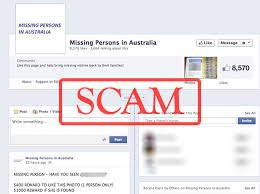
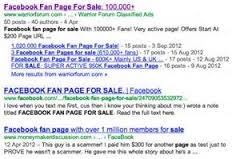
The process of gathering likes for a particular social media page through a combination of emotional exploitation, manipulation, and deception. This will involve CyberCriminals posting a string of posts designed specifically to capture followers for a Facebook page, which can then be later used for a variety of nefarious uses.
The list of followers can be used by the CyberCriminals for further spear-phishing, or sold to other CyberCriminals for their spamming use, or to marketing outfits.


 We Make I.T. Work!
We Make I.T. Work!

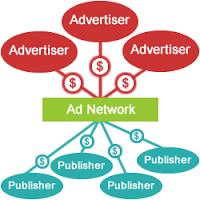 to one website at a time. Websites that want to make money, sell their advertising space to an Ad Network. Advertisers sign contracts with Ad Networks, which then displays the ads on the websites that they bought ad-space on. The Ad Network sits in the middle between the advertisers and the websites, and they manage the traffic and the payments.
to one website at a time. Websites that want to make money, sell their advertising space to an Ad Network. Advertisers sign contracts with Ad Networks, which then displays the ads on the websites that they bought ad-space on. The Ad Network sits in the middle between the advertisers and the websites, and they manage the traffic and the payments.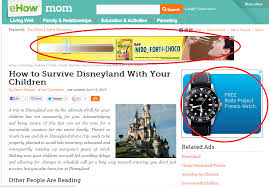 but the ads they give the Ad Network to display are Poisoned. Once an ad network is subverted, hundreds of millions of poisoned ads are displayed in real-time. Many of these ads initiate a drive-by attack without you having to do anything. If you browse to a page with a Poisoned ad on it, it runs the risk of having your PC encrypted with ransomware (which will cost you a minimum of $500 to rid yourself of, unless you have a very recent backup!). The attack infects the computer literally in seconds.
but the ads they give the Ad Network to display are Poisoned. Once an ad network is subverted, hundreds of millions of poisoned ads are displayed in real-time. Many of these ads initiate a drive-by attack without you having to do anything. If you browse to a page with a Poisoned ad on it, it runs the risk of having your PC encrypted with ransomware (which will cost you a minimum of $500 to rid yourself of, unless you have a very recent backup!). The attack infects the computer literally in seconds.




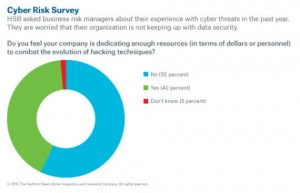
 Part of the problem, is that a controller likely set up the I.T. department, and no data security specialist has been appointed. Or, the “I.T.” person wears too many hats & can’t keep up with the latest malicious code and software patches.
Part of the problem, is that a controller likely set up the I.T. department, and no data security specialist has been appointed. Or, the “I.T.” person wears too many hats & can’t keep up with the latest malicious code and software patches.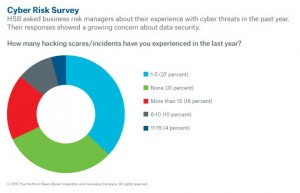
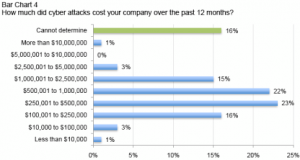



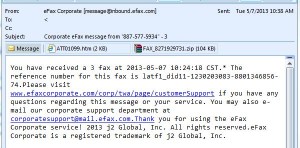
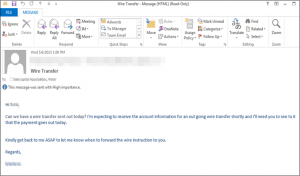 Previously known as “
Previously known as “


 Review:
Review: