Alert: Home Depot Hacked
After Target was hacked, execs at Home Depot Inc. put together a task force to prevent being the victim of a similar attack.
The task force recommended to fully encrypt any payment card information at all of the chain stores, but it wasn’t until months later that the work was begun.
The reason for this kind of action is that they thought they could defend against a hack like this, and apparently gave the wrong priority to the possibility that they had already been breached. Instead of prevention, they should have focused on the detection of the existing breach and getting the hackers out of their network.
The data breach is very similar to the breach that occurred at Target. The malware used to steal card data from Home Depot had the same code base as the tool used against Target, said the people who analyzed. (The data is generally vulnerable in the brief moment it passes into the system’s memory after the card is swiped.) After analyzing the malware, it was found that in both “malwares’, the code had Russian words in it.
It is a possibility that the hackers accessed Home Depot the same way they accessed Target, and used spear-phishing to access one of the Home Depot vendors.




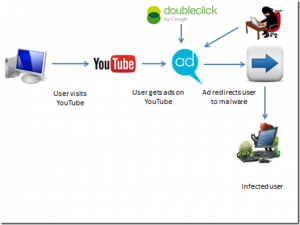
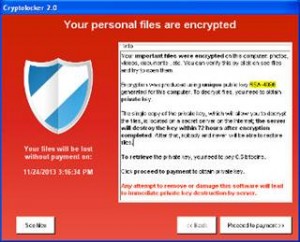
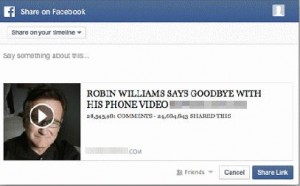
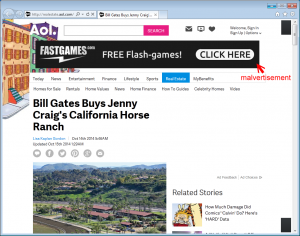 first video causes a redirect, an exploit kit located on a compromised website kicks in, finds a known unpatched vulnerability, and once found, executes ransomware code which locks all files and extorts $500. These exploit kits check for hundreds of known holes in mere seconds, so the “ad-network” threat just escalated to a much higher level.
first video causes a redirect, an exploit kit located on a compromised website kicks in, finds a known unpatched vulnerability, and once found, executes ransomware code which locks all files and extorts $500. These exploit kits check for hundreds of known holes in mere seconds, so the “ad-network” threat just escalated to a much higher level.