ALERT: Internet Capacity Warning
This new email scam is possibly fueled by the recent U.S. news that they have run out of IPv4 addresses in the U.S.
This new email scam is making the rounds at both homes and businesses.
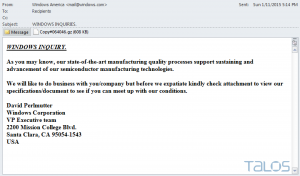
An email is currently being received, supposedly from “IT Services Support Department”, which claims that your Internet capacity is at 70%.
In order to rectify the situation, they request you to contact “Help Desk” support, for which they helpfully include a link.
Once you click the link, you are asked to leave your user name and password at the (bogus) “Help Desk” site.
You thoughtfully receive a “Thank You” page once you have completed all steps.
THIS IS A SCAM
They are trying to hijack your email account.
In the past, you may have received notifications from your Internet provider about your email account exceeding its maximum storage limit. However, the name of the service provider is always clearly visible, and they never ask you to click on a link to rectify the issue.
Do not click on links or attachments in emails from unknown or suspicious people.
If you suspect the item may be real, contact the company directly, from a number or email you look up elsewhere.





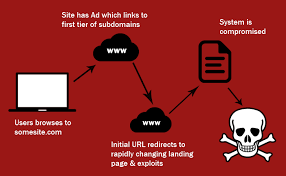
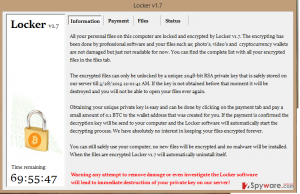
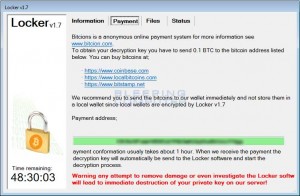 The files that are encrypted have the following suffix extension: .doc, .docx, .xlsx, .ppt, .wmdb, .ai, .jpg, .psd, .nef, .odf, .raw, .pem, .rtf, .raf, .dbf, .header, .wmdb, .odb, .dbf. Locker does not change the file extension, so users will simply receive error messages from their applications that the file is corrupted.
The files that are encrypted have the following suffix extension: .doc, .docx, .xlsx, .ppt, .wmdb, .ai, .jpg, .psd, .nef, .odf, .raw, .pem, .rtf, .raf, .dbf, .header, .wmdb, .odb, .dbf. Locker does not change the file extension, so users will simply receive error messages from their applications that the file is corrupted.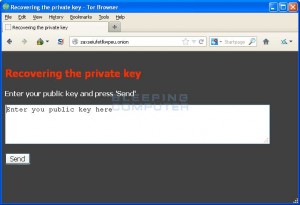
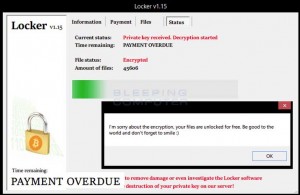



 ALERT:
ALERT: