ALERT: Bank Phishing Attack Using SMS Text Messaging
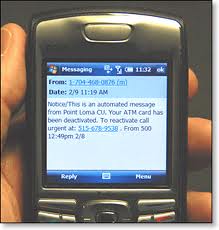
Victims receive a fake text from their ‘bank’ on their cell phone, stating there is a problem with their account. The text urges them to call a number in their own area code. When they dial the number provided, they receive the following automated message:
“Thank you for calling [name of bank]. A text message has been sent to inform you that your debit card has been limited due to a security issue. To reactivate, please press 1 now.” After pressing 1, the caller is prompted to enter the last 4 digits of their Social Security number, then the full card number and expiration date.
This is a mix of scams, known as “SMiShing” – phishing attacks sent via SMS text message – and voice phishing aka “vishing”, where people are directed to call a number that answers with a voice prompt, spoofing their bank and instructing the caller to enter confidential data.
NEVER call your bank from a number in a text or email.
Always double-check the phone number from your bank’s website.