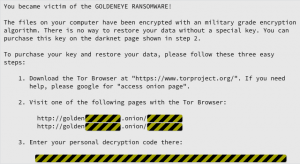
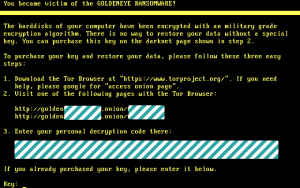
Not our everyday computer post around here, but I found it nice that in among all the Crowdfunding programs that give money to stupid things everyday like digging holes and filling them, GRAIL, a startup that hopes to try and catch the early stages of cancer before it takes hold in the body, is well on it’s way to 1 billion dollars and could climb to upwards of 1.8 billion. Its nice to see a feel good tech story once in a while instead of all the ransomware alerts that have become part of the daily culture. Here’s to hoping they are able to perfect the technology and make a difference!
Early cancer detection startup GRAIL closes on $900 million in Series B funding