ALERT: AshleyMadison Hack & Phishing Scam
A few months ago, the Adult Friend Finder (AFF) website was hacked and faced a multitude of phishing scams.
Now, AFF’s biggest competitor, AshleyMadison (AM), is facing the very same problem.
With 37 million registered users, AM’s online cheating site whose slogan is “Life is short. Have an affair”, is one of the most heavily-trafficked websites in America.
Large amounts of data has been stolen from AM, and has been posted online, by hacker(s) that go by the name “The Impact Team”. The data posted online includes sensitive internal data stolen from Avid Life Media (ALM), the Toronto-based firm that owns Ashley Madison as well as related hookup sites Cougar Life, and Established Men.
“The Impact Team” also claims to have completely compromised the AM’s user databases, financial records, and other proprietary information.
Avid Life Media released a statement yesterday reporting:
We have always had the confidentiality of our customers’ information foremost in our minds, and have had stringent security measures in place, including working with leading IT vendors around the world.
At this time, we have been able to secure our sites, and close the unauthorized access points. We are working with law enforcement agencies, which are investigating this criminal act. Any and all parties responsible for this act of cyber-terrorism will be held responsible. Using the Digital Millennium Copyright Act (DMCA), our team has now successfully removed the posts related to this incident as well as all Personally Identifiable Information (PII) about our users published online.
The Problem:
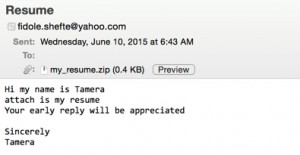
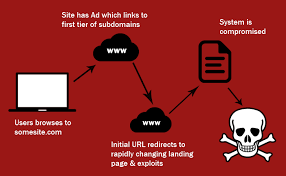
CyberCriminals are going to exploit this in many ways, sending spam, phishing emails, and possibly blackmail emails.
They are going to use social engineering tactics to scare people into clicking on infected links or opening infected attachments.
Any 1 of these 37 million registered users of AM, is now a target for a multitude of social engineering attacks. People that have extramarital affairs can be pressured into clicking on links that threaten to “out” them. Blackmail, spear phishing emails, emails with links to sites claiming to show people if their private data has been leaked, or emails with links claiming can prevent their private information from being leaked.
And you can bet that jilted spouses, divorce attorneys, and private investigators are undoubtedly going to pour over the leaked data.
BEWARE of any emails with threatening messages about AshleyMadison, or the company’s member list, or pictures, or information.
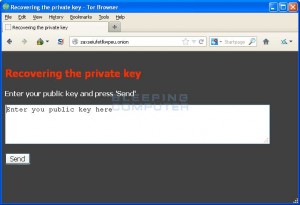
DO NOT click on any links or open any attachments.




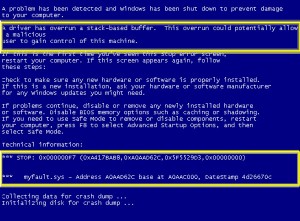
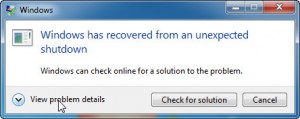 unexpected shutdown” message, you hit the jackpot. Click “View problem details” for technical information.
unexpected shutdown” message, you hit the jackpot. Click “View problem details” for technical information.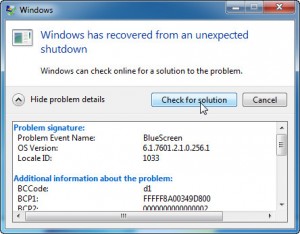
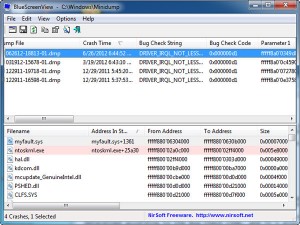 the free and portable program “
the free and portable program “


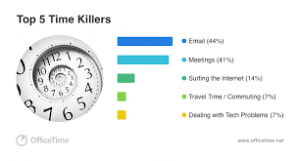

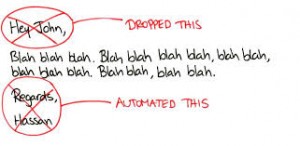 Think about it…how many of your emails could be trimmed of “fluff”, down to 5 sentences?
Think about it…how many of your emails could be trimmed of “fluff”, down to 5 sentences?





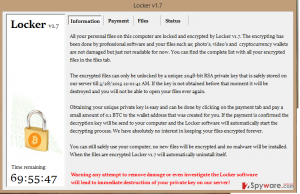
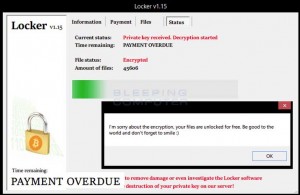
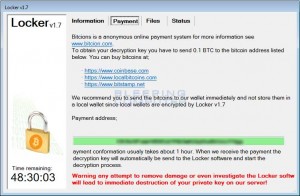 The files that are encrypted have the following suffix extension: .doc, .docx, .xlsx, .ppt, .wmdb, .ai, .jpg, .psd, .nef, .odf, .raw, .pem, .rtf, .raf, .dbf, .header, .wmdb, .odb, .dbf. Locker does not change the file extension, so users will simply receive error messages from their applications that the file is corrupted.
The files that are encrypted have the following suffix extension: .doc, .docx, .xlsx, .ppt, .wmdb, .ai, .jpg, .psd, .nef, .odf, .raw, .pem, .rtf, .raf, .dbf, .header, .wmdb, .odb, .dbf. Locker does not change the file extension, so users will simply receive error messages from their applications that the file is corrupted.