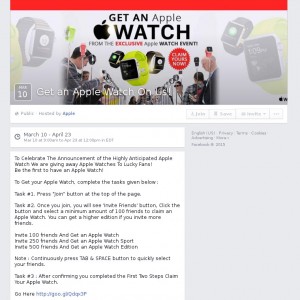
How-To:
Ensure Firewall Is Enabled In Windows7
- Click “Start”.
- Go to “Control Panel”, then “Security”.
- Click “Windows Firewall”.
- Click “Turn Windows Firewall On Or Off”.
- Input Administrator password, if prompted, or confirm the operation.
- Click “On” (Recommended).
- Click “Ok”.

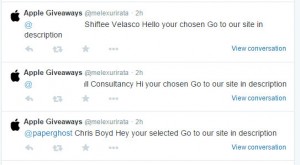 CyberCriminal gangs are setting up Twitter accounts named “Apple Giveaways”, targeting users that mentioned the smartwatch in their Twitter feed. They tell people they have been “chosen”, and promise them a free Apple Watch. All they ask them to do, is to click the link in the message. The link leads them to a series of links and instructions, leading them to other dubious web pages.
CyberCriminal gangs are setting up Twitter accounts named “Apple Giveaways”, targeting users that mentioned the smartwatch in their Twitter feed. They tell people they have been “chosen”, and promise them a free Apple Watch. All they ask them to do, is to click the link in the message. The link leads them to a series of links and instructions, leading them to other dubious web pages.