Peer-To-Peer
In a peer-to-peer network, all computers share equivalent responsibility for processing data.
A peer-to-peer network differs from a client-server network where certain devices (server) have responsibility for providing data and other devices (clients) consume the data.








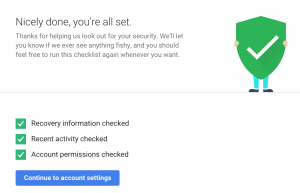 After you’ve gone through the checkup successfully, you’ll see 3 green checkboxes (see left) that confirm you’re eligible for the free storage and, more importantly, that you’ve taken steps to enhance your online safety.
After you’ve gone through the checkup successfully, you’ll see 3 green checkboxes (see left) that confirm you’re eligible for the free storage and, more importantly, that you’ve taken steps to enhance your online safety.