ALERT: WordPress Website Hack
An alarming number of websites built with popular website-building tool, WordPress, have been hacked, and are delivering the TeslaCrypt ransomware to unsuspecting victims.
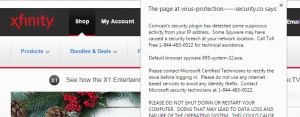
Malware researchers from Malwarebytes and other security firms have reported that a massive number of legit WordPress sites have somehow been compromised, and are silently redirecting visitors to sites with Nuclear Exploit Kit. As of press time, it is unclear how the WordPress websites are getting infected, but is highly likely that there is a new vulnerability that is being exploited in either WordPress, or one of its plugins.
Malwarebytes Senior Security Researcher Jérôme Segura stated in a blog released last week:
“WordPress sites are injected with huge blurbs of rogue code that perform a silent redirection to domains appearing to be hosting ads. This is a distraction (and fraud) as the ad is stuffed with more code that send visitors to the Nuclear Exploit Kit.”
The attack tries to conceal itself, and the code forces visitors to be redirected through a series of sites before dropping the ransomware payload. Once a WordPress server is infected, the malware also installs a variety of backdoors on the machine.
What to do if You Run WordPress:
- Update server Operating Systems (OS).
- Update WordPress.
- Delete any plugins you are not actively using, and update patches on any plugins you currently use.
- Update all your WordPress instances at the same time to prevent cross-infections.
- Lock down all WordPress instances with a very strong password, as well as the WordPress 2-factor authentication
How to Protect Your Website Visitors:
- Keep workstation Operating Systems (OS) and 3rd party apps updated at all times.
- Backup your data and keep daily off-site backups. TEST your backups, and if your restore function actually works (this is often overlooked).
- Provide end-users with the 64-bit version of Google Chrome if possible.
- Run the latest V5.5 of Microsoft’s Enhanced Mitigation Experience Toolkit (EMET) on workstations.
- Provide Security Awareness Training.

Not sure if your company is safe? Ask us for a FREE Network Security Assessment!
Check out our “Email Red Flags” for what to watch for in suspicious emails.