ALERT: Fake Retail Apps for iPhone and Android
ALERT: Fake Retail Apps for iPhone and Android
The New York Times has issued a warning to the public about a new kind of ID theft: App ID Theft…just in time to deceive holiday shoppers!
Every holiday season, “retail apps” become popular. Starbucks started the trend, but others have since copied.
Both Apple’s App Store and Google Play are getting crowded with fake “imposter” apps.
The counterfeiters are masquerading as big retail chains like Dollar Tree and Foot Locker, big department stores like Dillard’s and Nordstrom, online product bazaars like Zappos.com and Polyvore, and luxury-goods makers like Jimmy Choo, Christian Dior and Salvatore Ferragamo.
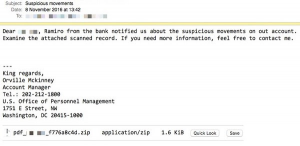
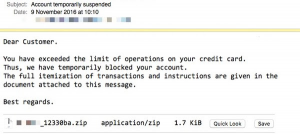
The fake apps trick you into dowloading them to your smartphone or tablet, and ask you to load your credit card.
5 Things to Remember When Downloading Apps:
- Be very judicious in deciding what app to download. Better safe than sorry!
- If you decide to download an app, first check the reviews. Apps with few reviews, or bad reviews, are a big Red Flag!
- Never click on a link in any email to dowload a new app. Only go to the website of the retailer to get the link to the legit app on the AppStore or Google Play.
- Give as little information as possible if you decide to use an app.
- Be very, VERY, reluctant to link your credit card to any app!
For more information on the New York Times’ warning, go to: http://www.nytimes.com/2016/11/07/technology/more-iphone-fake-retail-apps-before-holidays.html