ALERT: New Ransomware Also Steals Your Bitcoins
With the rash of new ransomware strains out there, you knew they were going to up the ante somehow…
CryptXXX is built by the same CyberCriminals that are behind the Revelton malware. It is an attempt to one-up the release of the Locky ransomware by their CyberCriminal Competitors.
CryptXXX currently spreads through the Angler Exploit Kit which infects the PC with the Bedep Trojan, which drops information theft software on the PC, then adds professional-grad encryption adding a “.crypt” extension to the filenames.
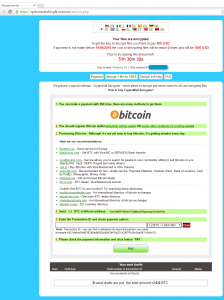
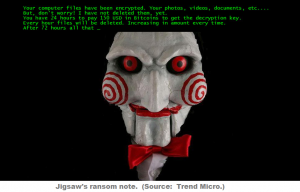
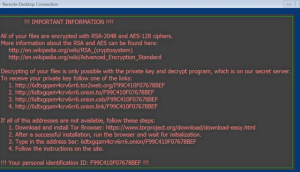
This ransomware encrypts files locally, and on all mounted drives, and demands $500 Bitcoin/PC to unlock the encrypted files. However, they continue to add insult to injury by also stealing Bitcoins, as well as a large range of data.
CryptXXX tried to avoid detection through “random delayed” execution (which attempts to easily connect the infection to the delivery vector), anti-Virtual Machine, and anti-analysis functions (eg. checking CPU names in the registry, monitoring for mouse events).
The CyberCriminals behind this ransomware is highly skilled and experienced, which means this is professional-grade ransomware. Proofpoint researchers report “Those [ransomware infections] associated with more experienced [CyberCriminals], (such as Locky) have become widespread quickly…Given Revelton’s long history of successful and large-scale malware distribution, we expect CryptoXXX to become widespread. Based on the large number of translations available for the [Bitcoin] payment page, it appears that the Revelton team shares those expectations.”
The ransomware will initially be spread through drive-by downloads, but a deluge of phishing emails can be expected to follow shortly.
What Can You Do to Avoid Becoming a Ransomware Victim:
- Backups. Backups. Backups. Maintain current, and reliable backups of all pertinent files. Nothing beats a good, reliable backup! Backing up your data now can prevent a lot of expensive headaches in the future.
- AntiMalware Software. Regularly run AntiMalware software to block known strains of ransomware.
- Update. Update. Update. Keep all hardware, software, and Operating Systems up-to-date.
- Educate. Educate. Educate. Make sure employees and coworkers know about current viruses/malware, and what to look for. Print & post our “Red Flag Emails” for easy reference on what to look for in scam emails.
- Install Ad Blockers When Possible. uBlock Origin is a great ad blocker for Chrome and other browsers.
- Block Extensions via Email. A good spam blocker will usually handle this for you.
- Limit permissions. Allow “Read/Write Access Only” when necessary.
- Avoid mapping network shares. If you have to use them, hide them whenever possible. This is sometimes as simple as appending a “$” to your share name.