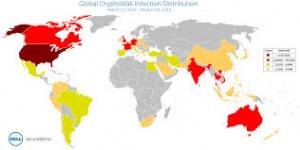
In many a budget meeting, the idea is thrown around “do we REALLY need IT?” Well, if this article doesn’t convince you that I.T. is invaluable, nothing will…
There is a new Ransomware strain out there:
A true self-replicating parasitic virus called
VirRansom!
As the name implies, it is a hybrid.
It combines CyptoWall-like functionality, with active self-replicating virus infections of all files it can find, with the cybercrime Reveton family of malware’s locking of the PC’s main screen.
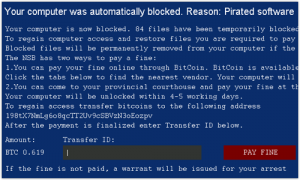
Oh yea, it also demands 0.619 Bitcoin to let you back in. Ouch.
SophosLabs states:
“Worms vs. Parasitics: Most worms leave you with one, or perhaps a handful, of infected files that weren’t there before and need to be deleted.
Parasitic viruses, in contrast, may leave you with hundreds, or thousands, or more, of infected files on each computer. If you leave even one of those infected files behind after a clean-up, the infection will start up all over again.
Worse still, the infected files can’t just be deleted, because they are your own files that were there before the infection started. That makes cleanup even trickier.“
Before you go into full-fledged panic mode, there is good and bad news with this virus.
You seem like you could use some good news at this point…
The Good News:
The file encryption is not as advanced as CryptoWall, as they key to decrypt the files is contained in the malware itself. Your antivirus should soon be able to decrypt the files and restore them (hint: keep up with updates!), unless the bad guys are constantly changing the encryption keys. In which case, it may take a day or more before your antivirus catches up.
The Bad News:
This is a full-fledged virus. It will spread across your network, and doing a less-than-perfect job on the disinfection can easily lead to reinfection of your whole network.
CryptoWall-encrypted files that you can’t or don’t decrypt are harmless garbage forever, but you can delete them.
With VirRansom, files that you don’t decrypt are still recoverable, but also still actively infectious.
It gets even nastier: You can expect a VirRansom 2.0 soon, where they might implement “new features” such as:
- industrial-strength encryption like Crypt0Wall where you only get the decryption keys after payment
- infection of your email server, where emails are converted to a worm for maximum dissemination of their malcode. (Think of the legal ramifications this may have on your business!)
You can mitigate these types of threats through both technical measures, and enforcing your company’s computer use policy.
Some technical measures:
- The 1st thing you need to do is test the Restore function of your backups, and make sure it works. And have a full set of backups offsite.
- Start thinking about asynchronous real-time backups, so you can restore data files with a few mouse clicks.
- Get rid of mapped drives and use UNC links for shared folders.
- Whitelisting software, which only allows known-good executables to run, starts to look more attractive, as more and more of these viruses/malware surface.
Looking at the security policy angle, it’s time to actually enforce best practices:
- Implement (and enforce) an “Internet Acceptable Use Policy or IAUP”. This informs your employees what is (and isn’t) acceptable for use of their work computers while utilizing the internet. They sign this document stating that they will use work computers within the parameters that are set out in the IAUP.
- Prevent these types of infections to begin with, through effective Security Awareness Training. The infection vector (think “patient zero”) is your end user (ie. anyone in your company that uses a computer at any time) opening up an attachment or clicking on a link. Employees need to be not only informed, but trained on computer security. Call this your “Human Firewall”.





 This lures you with messages from friends, or sometimes malicious ads on your wall, to check who has looked at your profile. But when you click, your profile will be exposed to the scammer, and
This lures you with messages from friends, or sometimes malicious ads on your wall, to check who has looked at your profile. But when you click, your profile will be exposed to the scammer, and 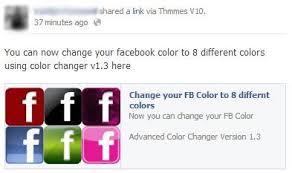 This tries to trick you to personalize your Facebook page. However, it also leads you to phishing sites, deceives you to share the app with your friends, and infects your mobile devices with malware. Stay away from this app!
This tries to trick you to personalize your Facebook page. However, it also leads you to phishing sites, deceives you to share the app with your friends, and infects your mobile devices with malware. Stay away from this app!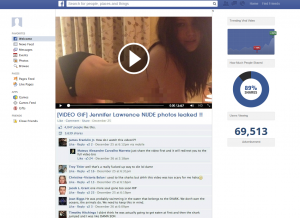 There are tons of fake naked videos being posted all the time, using names of celebrities like Rihanna or Taylor Swift, that sometimes make it through Facebook moderators. These scams are in the form of an ad or a post, and have a link to bogus YouTube videos. That site then claims your Adobe Flash player is broken, and says you need to update it – but malware is installed instead!
There are tons of fake naked videos being posted all the time, using names of celebrities like Rihanna or Taylor Swift, that sometimes make it through Facebook moderators. These scams are in the form of an ad or a post, and have a link to bogus YouTube videos. That site then claims your Adobe Flash player is broken, and says you need to update it – but malware is installed instead! Computer bad guys often try enticing titles like “Not Safe For Work” or “Scandalous” to lure you into clicking on these videos. You then get automatically redirected to phishing sites that steal your personal information.
Computer bad guys often try enticing titles like “Not Safe For Work” or “Scandalous” to lure you into clicking on these videos. You then get automatically redirected to phishing sites that steal your personal information.


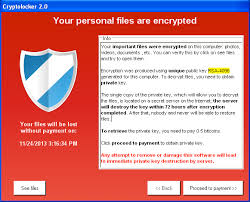
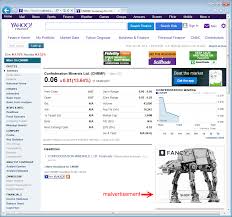
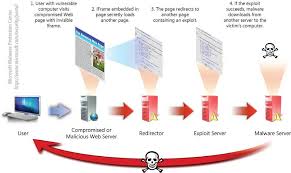 people who run unpatched versions of Adobe Flash. The poisoned ads silently ‘pull in’ malicious exploits from the FlashPack Exploit Kit, hence the “drive-by-downloads”.
people who run unpatched versions of Adobe Flash. The poisoned ads silently ‘pull in’ malicious exploits from the FlashPack Exploit Kit, hence the “drive-by-downloads”.