ALERT:
Email Attachment “Fax”
CryptoWall 3.0
This email scam is the latest CryptoWall attack that has affected businesses world-wide.
An email is sent, which has an innocent-looking email attachment that claims to be a fax report from your own business or home.
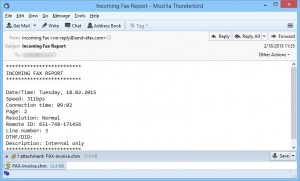
If you receive an email that claims to be a fax report, that seems to come from your own domain/business/home, but the link ends in “.CHM”,
The email attachment link will look similar to the one below:
DO NOT OPEN,
and
DO NOT FORWARD.
DELETE THE EMAIL IMMEDIATELY!
After you delete the email, warn I.T. that the email sits in your “Deleted” items.
If you click on the link to open it, it will download malware, which will lock up all your files,
and potentially all files of everyone else in your business or organization.
The CyberCriminals responsible for this scam, then demand a $500 Bitcoin ransom to get your files back.
This malware is being sent in waves, attacking computers all over the world.
We highly recommend to add “.CHM” files to the list of potentially malicious extensions in your spam filters.
Got Computer Bugs?
Call 1-204-800-3166
For Cyber-Extermination!












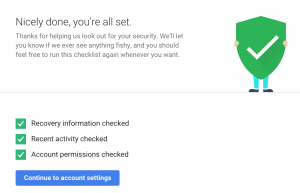 After you’ve gone through the checkup successfully, you’ll see 3 green checkboxes (see left) that confirm you’re eligible for the free storage and, more importantly, that you’ve taken steps to enhance your online safety.
After you’ve gone through the checkup successfully, you’ll see 3 green checkboxes (see left) that confirm you’re eligible for the free storage and, more importantly, that you’ve taken steps to enhance your online safety.